Ensure a reliable audit trail
with qualified timestamping

In an increasingly demanding regulatory environment (AI Act, GDPR, NIS2, MiFID II/MiFIR, DORA, MiCA, Data Act…), businesses must demonstrate the traceability, authenticity, and above all the integrity of their critical data.
Qualified timestamping, as defined by the eIDAS regulation, enables compliance with these requirements. By recording the fingerprint (hash) of each strategic event or data point via API, organisations gain legally admissible evidence: the date and time are legally presumed accurate, and the integrity of the content is guaranteed.
Qualified Timestamping:
twofold benefits
Legal advantage
Qualified eIDAS timestamping provides legally admissible evidence during inspections, audits, or litigation. Under the eIDAS regulation, it carries a presumption of reliability and shifts the burden of proof to anyone who disputes it.
Operational advantage
Qualified timestamping helps streamline verification processes and reduces exposure to penalties when compliance can be demonstrated.
Rising data volumes
to trace and prove
Evidency’s qualified timestamping integrates at scale via API into your business systems to ensure a reliable audit trail across all critical data flows:
- ERP / Finance: orders, invoices, accounting closures, journal entries
- Trading / MiFID: orders, executions, cancellations, voice or instant messaging records
- AI & data: dataset versions, models, artefacts, inference logs
- Security / Incidents (NIS2 / DORA): SIEM logs, incident timelines, alert notifications
- R&D / Industry: specifications, test reports, validations, PLM/MES, laboratory notebooks
- Legal / Contracts: consents, NDAs, amendments, proof of notification
- Crypto / MiCA: operational logs, transactions, compliance reports
Depending on the size and sector of the organisation, these flows can represent several million, or even tens of millions, of events per year. Qualified timestamping automates the generation of legally admissible proof, ensuring complete traceability that is enforceable and compliant with European regulations.

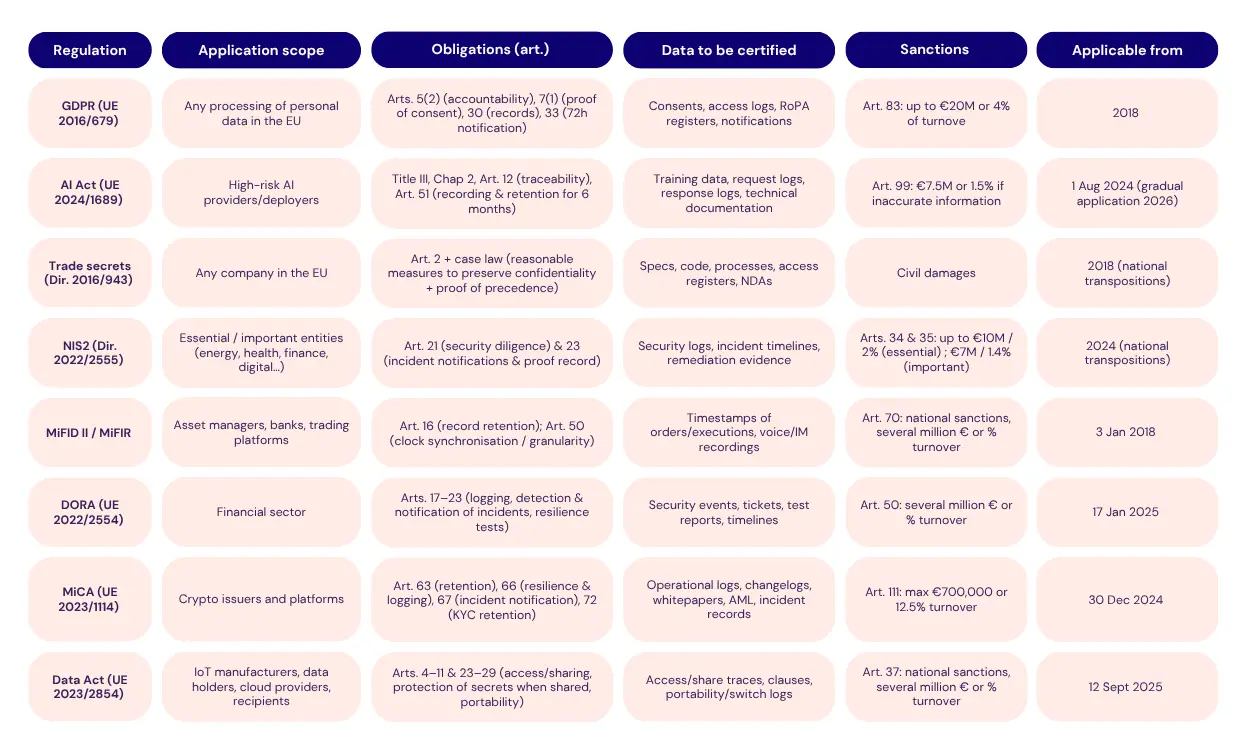
Overview of regulatory requirements
for digital evidence
How does it work?
Step 1
Identifying the company’s specific requirements
Step 2
Connection between the Evidency system and the client system via a REST API
Step 3
The client system hashes the data and sends the hash to be timestamped
Step 4
Evidency timestamps the unique hash and returns the timestamp token to the client
Speak with our legal experts for guidance on the regulations affecting your sector